Oct 22, (this is a guest post from Tenox). VxWorks is an embedded operating system that typically runs on things like Mars probes, Boeing or. Oct 22, Powering billions of intelligent devices, VxWorks® delivers an Wind River treats VxWorks security seriously .. HD Moore - Fun with VxWorks. Aug 2, Back in June, I decided to spend some time looking at the VxWorks For more information, see my Fun with VxWorks presentation (PDF) from.
| Author: | Turr Tarr |
| Country: | Peru |
| Language: | English (Spanish) |
| Genre: | Automotive |
| Published (Last): | 6 October 2024 |
| Pages: | 400 |
| PDF File Size: | 5.94 Mb |
| ePub File Size: | 2.98 Mb |
| ISBN: | 684-2-71361-941-1 |
| Downloads: | 76017 |
| Price: | Free* [*Free Regsitration Required] |
| Uploader: | Mular |
I would also vxwoks to thank the security response team at Rockwell Automation, who took both issues seriously, did a deep assessment of their entire product line, and shared their findings.
Go to this page: Wind River Workbench http: Hi Julien, Thank you for your question. One of the Metasploit modules I wrote for the WDB Agent performs a complete physical memory dump of the target device.
If you want to do and learn more stuff, you need to download evaluation of VxWorks Fuj and spin up the VxWorks Simulator, or build your own target.
The Metasploit Framework SVN tree has been updated with a set of modules for detecting vulnerable systems and performing a remote memory dump.
Notify me of followup comments via e-mail. Of this set, oversystems were found with the WDB witn exposed. VxWorks debug server default port Found to be running on a number of devices in production.
Fun with VxWorks MILS 2.1
WindRiver has an evaluation target that you can run on an Intel CPU, meaning you can spin it up on your favorite hypervisor at home. The Rapid7 Nexpose engineering team has created a check for this vulnerability and made this available through the standard product update mechanism.
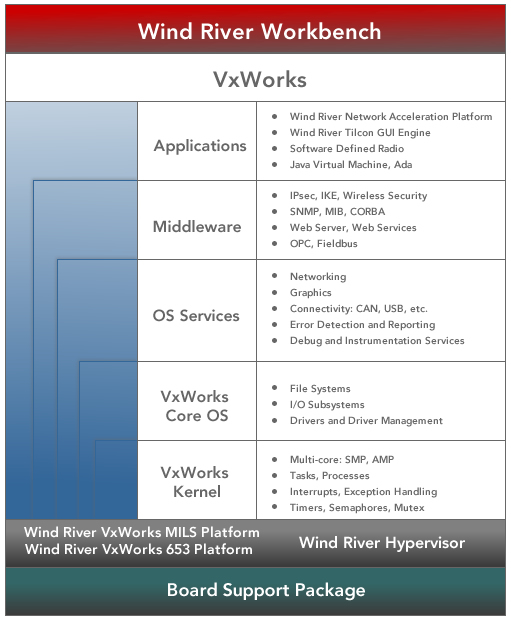
After digging around in the DShield database, it became obvious that an unknown party had already spent most of scanning for this service. VxWorks itself is essentially a monolithic kernel with applications implemented wth kernel tasks.
Take a memory image before Make config changes to enable remote admin Take another snapshot Rollout changes to the remote devices Memory Scraping Locate sensitive information in memory Write a scanner to find it Have Fun! You guys kick ass and did an amazing job at both notifying the affected vendors and standing your ground on the disclosure schedule.
I noticed hardcoded credentials in the memory dumps obtained from a wide range of devices. To make matters worse, the number of passwords that are actually reasonable to type not high or low ascii fit within about 8, permutations. Finally, I would like to thank the fine folks at CERT, who agreed to take on a vendor coordination task in the 60 days leading up to the summer conferences. These posts are in notes form and are written live during a talk.
Fun with VxWorks MILS | Wind River Blog
VxWorks is an embedded operating system that typically runs vxworkz things like Mars probes, Boeing or Apache helicoptersbut today you can run it too! The author has mentioned that it includes the steps to run it on Vmware, i have the BSPbut i need the steps to do it.
They will be performing at VxWorks has been used to power everything from the Apple Airport Extreme access points to the Mars rovers and the C Hercules aircraft.
Presumably, this was done so that anyone with access to an unencrypted firmware image could not login with the backdoor account just by reading the clear-text password. If yes kindly provide the link to download. Aug 02, 5 min read.
You can run VxWorks too! – Virtually Fun
Authenticate this comment using OpenID. This credential set is baked into the firmware image, and while this backdoor account can be removed by application code calling loginUserDeleteit is quite common for these credentials to be left in place for production builds.
View Cookie Policy for full details. This means that all tasks generally run with the highest privileges and there is little memory protection between these tasks at least with version 5. Learn how your comment data is processed.
Porting from VXWorks to Linux is not fun…
The two bugs mentioned in this qith are just the tip of the iceberg and there is a lot more work left to do before the VxWorks platform is as tested as it needs to be. Pulling the Admin password out of the memory Apple Airport used to suffer from this until it was patched.
Now owned by Intel Most widely deployed embedded OS based on info Supports various hardware platforms Each application run as kernel threads Little memory protection between applications Everything runs with the highest privileges… not necessarily the highest priority Used in systems from VoIP phones through to Fibre Channel switches.
